Phishing isn’t the only way attackers steal your credentials anymore — today’s threats target your session tokens.
In this SYNACK Time video, we explore Check, a free and open-source browser extension built to defend against Microsoft 365 token theft and Adversary-in-the-Middle (AiTM) attacks.
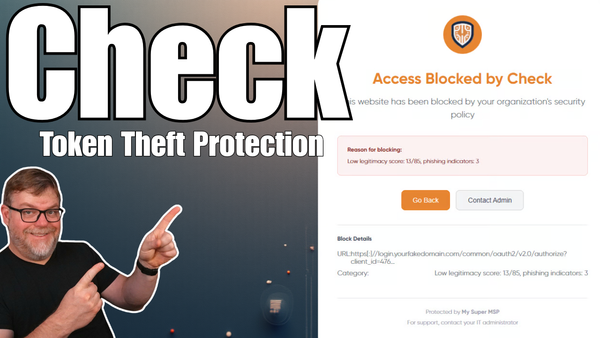
Developed by CyberDrain, Check gives your browser the intelligence to spot malicious login pages and prevent attackers from capturing tokens, even if credentials are entered. It’s smart, privacy-first, and built specifically for modern Microsoft 365 environments.
What Is Check?
Check is a browser extension designed to detect and block token-stealing AiTM attacks targeting Microsoft 365.
Instead of relying solely on user awareness or server-side filtering, Check monitors the browser environment itself, identifying when a login page has been tampered with or redirected through a malicious proxy.
Key highlights:
- Detects and blocks token interception attempts
- Prevents Adversary-in-the-Middle (AiTM) exploitation
- Works seamlessly with Chrome, Edge, and other Chromium-based browsers
- Supports CIPP integration for managed service providers
- Can be white-labeled and branded for enterprise deployment
- Collects no telemetry, no analytics, and no user data
For MSPs, Check provides a lightweight, auditable way to improve Microsoft 365 security across multiple tenants.
What You’ll Learn in the Video
This SYNACK Time walkthrough dives deep into how Check works — and why it’s an essential addition to your Microsoft 365 defense stack:
- Understanding token theft and AiTM attacks
- Demonstrating how attackers bypass traditional phishing filters
- Installing Check for Chrome and Edge
- Customizing and branding Check for your organization
- Integrating with CIPP for MSP scalability
By the end, you’ll see firsthand how Check blocks modern token theft attempts and adds a critical defensive layer right where users log in.
Why Token Theft Matters
Attackers no longer need your password — they just need your token.
Once they steal it, they can access Microsoft 365 accounts without triggering MFA or security alerts.
Check helps neutralize this attack vector by analyzing session behavior and blocking malicious token handoffs before they ever leave the browser.
For MSPs, this means fewer compromised tenants and fewer sleepless nights managing incident fallout.
Resources
- Check Documentation: https://docs.check.tech
- Check on GitHub: https://github.com/cyberdrain/Check
- CyberDrain Blog: https://cyberdrain.com
- SYNACK Time: https://synacktime.com
- SYNACK Time GitHub: https://github.com/SynAckTime
- Self-Hosting on a Budget (YouTube): Watch here